 English
English
 中文
中文
EM Eye investigates a cybersecurity attack where the attackers eavesdrop on the confidential video data of cameras by parsing the unintentional electromagnetic leakage signals from camera circuits. This happens on the physical/analog layer of camera systems and thus allows attackers to steal victim's camera data even when perfect software protections (e.g., unbreakable passwords) are all in place. Exploiting the eavesdropped videos, attackers can spy on privacy-sensitive information such as people's activities in an enclosed room recorded by the victim's home security camera. Check out the demo video below.
The research paper of EM Eye is to appear at The Network and Distributed System Security Symposium (NDSS) 2024. The PDF and reference information can be found below.
@inproceedings{long2024emeye,
title={EM Eye: Characterizing Electromagnetic Side-channel Eavesdropping on Embedded Cameras},
author={Long, Yan and Jiang, Qinhong and Yan, Chen and Alam, Tobias and Ji, Xiaoyu and Xu, Wenyuan and Fu, Kevin},
booktitle={Network and Distributed Systems Security (NDSS) Symposium},
year={2024}
}

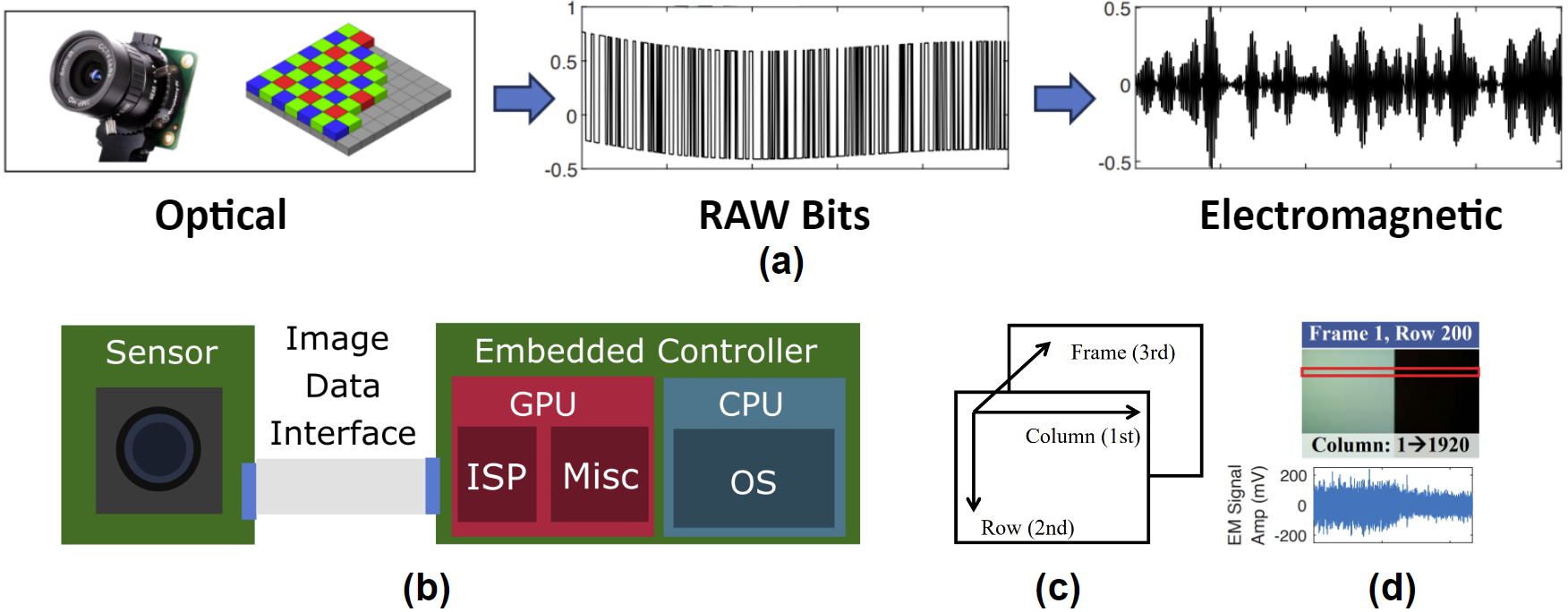
Cameras' imaging sensors transmit unprotected, plain video data in a completely deterministic manner to downstream processors such as GPUs and CPUs. While data encoded as bits cause alternating, image-specific electromagnetic (EM) fields around the camera circuits, the data transmission cable connecting the imagers and processors act as an unintentional radio antenna that broadcast the EM waves to adversaries. Attackers can then receive the EM leakage using an eavesdropping antenna and reconstruct the camera outputs by analyzing the EM signals, as demonstrated below. The quality of the reconstructed images can be further improved using deep learning-based signal processing methods.
EM Eye's causality analysis focused on the example of the trending embedded camera data transmission interface: MIPI CSI-2. Other similar interfaces are also be susceptible.

Consumer Electronics: Our non-exhaustive tests with 12 different models of smartphone cameras, dash cams, and home cameras show that this this vulnerability widely exists in commercial off-of-the-shelf (COTS) camera devices. The seriousness of information leakage depends on several factors of each camera device, such as the size and shielding of their transmission cables/circuits.
IoT Development Platforms: Almost all of today's IoT dev platforms are susceptible to this attack. We could eavesdrop on Nvidia Jetson, and Asus Tinkerboard, and Raspberry Pi cameras at very long distances: DIY home security cameras using Raspberry Pi may not be such a good idea!
Eavesdropping Attack Scenario Case Studies: With commercially-available eavesdropping equipment, attackers may be able to eavesdrop on smartphone cameras from up to 30 cm away, and eavesdrop on dash/home/IoT cameras from several meters away. We investigated the following attack scenarios of EM Eye:
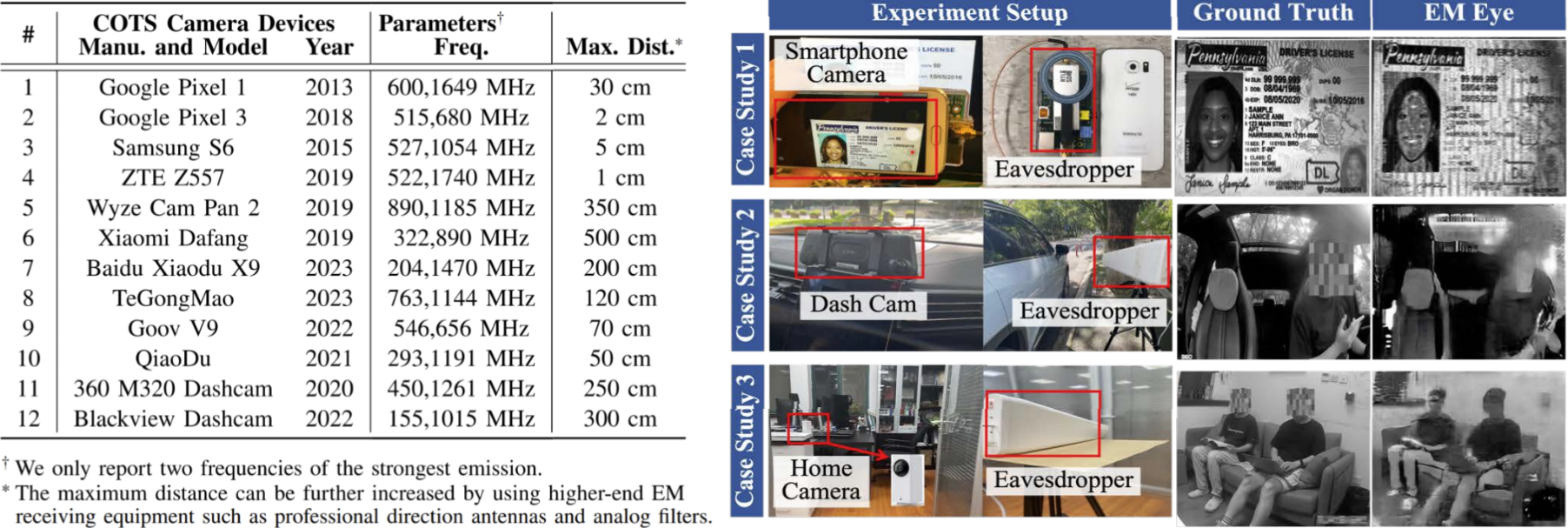
Fig. 3: The susceptible camera devices we found and their maximum eavesdropping distances using eavesdropping equipment that's worth less than $3k. With closer distances (e.g., for smartphones), attackers may install hidden antennas around smartphones such as in the form of compromised power banks. With longer distances (e.g., for dash/home cameras), attackers can eavesdrop on these cameras through doors and walls.
Below is a list of equipment we used for the experiments.
(1) Software Defined Ratio (SDR): Ettus USRP B210 USRP, ~$2100.
(2) Low Noise Amplifier (LNA): Foresight Intelligence FSTRFAMP06 LNA, ~$200.
(3) Directional Antenna: A common outdoor Log-periodic directional antenna (LPDA), ~$15.
(4) A laptop, of course.
Note that the equipment can be replaced with cheaper counterparts. For example, USRP B210 can be replaced with RTL-SDR that costs ~$30.
To reproduce the attack: our GitHub repository provides the codes and instructions for reproducing and understanding the attack. We have prepared a ready-to-use software tool that can produce real-time reconstructions of the eavesdropped videos with EM signal input from the USRP device.
EM and Eye stand for electromagnetic and camera respectively. Essentially, this attack exploits the EM side channel leakage from camera circuits to eavesdrop on the images seen by victim's cameras
Whenever the camera is on, it starts leaking information as EM waves. This does not even require that the camera is actually storing the video. The eavesdropping distance results suggest that EM Eye may pose the most serious threats to dash cams and home cameras. Home cameras, in particular, can be eavesdropped on from the other side of a wall. Many smart home cameras are also kept on all the time to support motion detection features, which could cause additional concerns.
Camera is just one type of sensors that transmit unprotected data. Similar vulnerabilities on other types of sensors are also observed and investigated in our ongoing works. We are systematically characterizing the emerging threats of sensor side channels.
Ideally, cameras should have no unintentional EM emissions or use encrypted data transmission between the semiconductor sensor and downstream processors so that attackers cannot infer camera data by analyzing camera's EM leakage. In practice, we found that factors contributing to higher strengths of EM leakage includes longer transmission cables, poor EM shielding, higher operating voltages, etc. So designers can consider changing these design parameters accordingly to minimize leakage.